
Gaining Anonymity: The Tor Network & Tor Browser Bundle
My first step in looking at anonymity is making use of the TBB and the Tor network. Tor was released in 2002 and has since evolved into a tool that is used by millions of people worldwide. Tor enables users to browser the internet, chat with other people, and access “hidden sites” (websites with .onion appended to the end of them that generally cannot be viewed in a normal browser over regular internet). The Tor network is used by freedom rights activists, privacy advocates like myself, whistleblowers, journalists, and even criminals doing illegal things like selling drugs. Because of that last little bit, I dislike the fact that Tor shields individuals so well from being caught, but I also feel that it is a great tool for protecting your privacy in a world where we are constantly being monitored and watched. It’s a hard boat to be in when on one side of the river, you have people literally fighting for their right to freedoms and free speech, but only the other side of the river, you have people doing ridiculously illegal things.
To understand how Tor works, you first should see this picture published by the EFF:
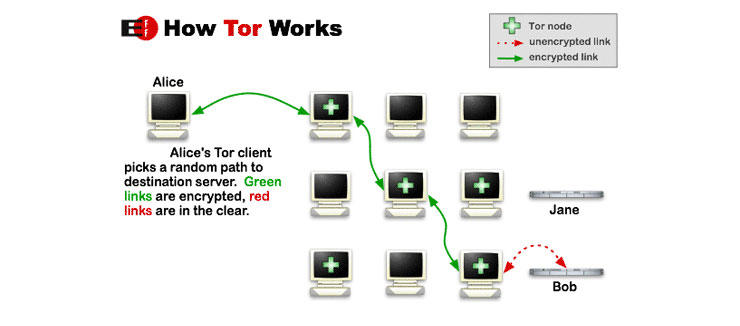
Basically you are connecting to a network that is routed through three separate servers from around the world before sending out data from your computer to a website and then returning data from said site back to your system. These servers are referred to as “nodes” and make sure that your data is fully encrypted while in transit to the destination site. If the site you are connecting to over Tor does not make use of HTTPS (SSL Certificate for encryption), then the connection between the last node (Exit Node) to the website’s server will not be encrypted but you will still be anonymous to the site.
The encryption that happens is done at the packet level see:
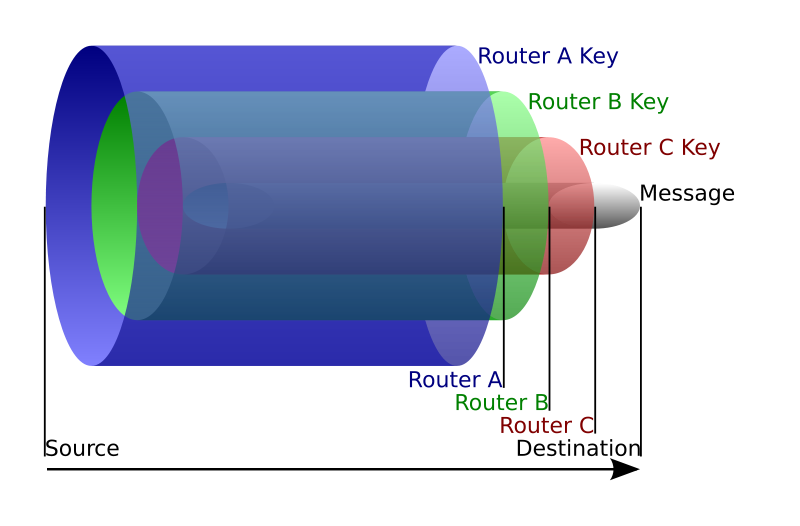
Which means information isn’t viewable even if it is intercepted in the middle. There are a few known attacks on .onion sites but many of them fall into the category of failing to correctly setup the server hosting the site. A prime example of this would be with a hidden service known as doxbin. The server it was hosted on was seized after 3 months of denial of service attacks to pinpoint its location.
For more information on the different attacks against Tor Hidden Services, see: https://www.google.com/search?q=.onion+attacks. Google, and likely your Internet Service Provider are likely monitoring search results. It would be interesting to know just what this logging looks like. Alternatively, you can type “Attacks on Tor” or “.onion attacks” into Searx.me which is a more privacy respecting search engine. The only attack I know of against Tor users is to exploit plugins they have installed, JavaScript/Flash in the browser, or by profiling them and getting bits and pieces of information about them over time. There could however be zero-day exploits available to Government Bodies that we are unaware of. So using a VPN behind Tor isn’t such a bad idea.
Related Categories on PrivacyTools.io:
To get the most out of Tor, you should refer to the section on Browsers, the add-ons to install and preferences to change in your about:config. But I would like to CAUTION YOU that installing a bunch of add-ons increases your chances for exploits to affect you and also actively increases your fingerprint. The idea behind using Tor to gain anonymity is to be like everyone else… so just disabling JavaScript/Flash but leaving everything else rather Plain-Jane is likely going to be your best bet. The people behind Tor have developed it to be secure and anonymous with a fresh install so the only thing you really have to do is go over the settings to make use of the built in features.
